. There are multiple ways to verify electronic authenticity. Heres an outline of the most popular digital authentication methods in the enterprise today
digital authentication system. Unique passwords.. Authentication - Wikipedia. Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or things identity, authentication is the process of verifying that identity
digital authentication system. [1]. List of Top Authentication Systems 2023 - TrustRadius
digital authentication system. 1 WatchGuard AuthPoint 199 reviews Top Rated AuthPoint Total Identity Security provides businesses with a solution to protect user accounts and credentials. With multi-factor authentication, password management, and dark web credential monitoring, AuthPoint mitigates the risks associated with workforce credential attacks.… Try AuthPoint 2 Cisco Duo. The IAM Leaders Guide to Biometric Authentication - Gartner. Most enterprise workers are all too familiar with the challenges of digital authentication. Whether its returning from a week off from work only to be locked out of a computer due to a password change policy or a lost security token, forcing a call to the IT department, authentication methods are often at odds with ease of access. Enterprise security leaders continue to seek approaches to .. Digital ID: A key to inclusive growth | McKinsey
digital authentication system. Digital identification, or "digital ID," can be authenticated unambiguously through a digital channel, unlocking access to banking, government benefits, education, and many other critical services. The risks and potential for misuse of digital ID are real and deserve careful attention. When well-designed, digital ID not only enables civic and social empowerment, but also makes possible .
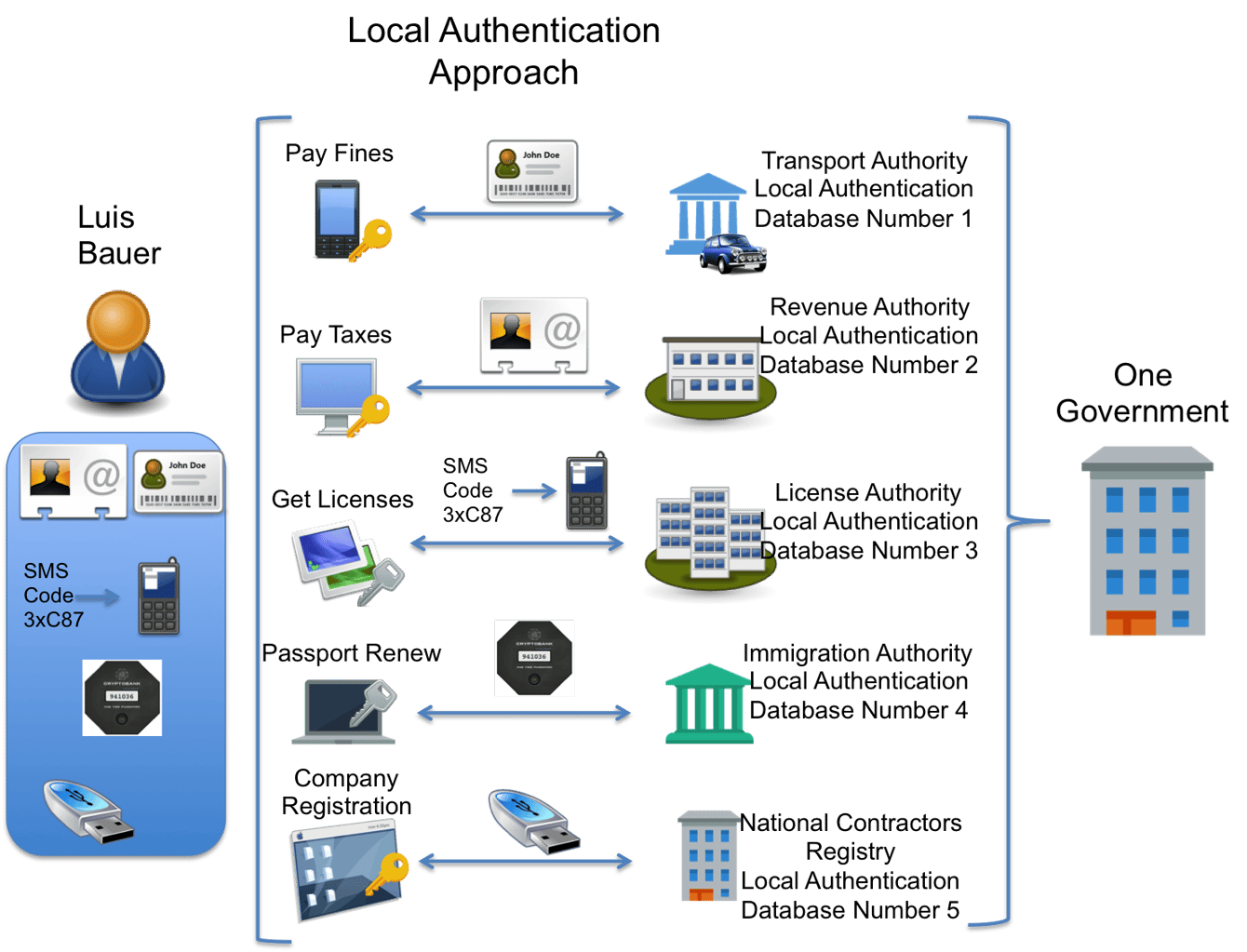
digital authentication system. NIST Special Publication 800-63-3. A digital authentication system may incorporate multiple factors in one of two ways: The system may be implemented so that multiple factors are presented to the verifier; or; Some factors may be used to protect a secret that will be presented to the verifier.
digital authentication system. Advantages & Disadvantages of Authentication Systems | Mitek. Blog Costs and benefits of authentication June 8, 2021 As technology improves, cybercriminals are also getting smarter. A new dark web audit revealed 15 billion stolen credentials from 100,000 data breaches circulating among cybercriminals.. Digital authentication - factors, mechanisms and schemes
digital authentication system. Similarly, digital authentication is about having suitably secure mechanisms in place to be able to confirm whether an individual or online user is who they say they are. This article gives a comprehensive insight into digital authentication and the IT-enabled processes and architectures needed.. Tips for Cost-Effective Evaluation of Digital Authentication Systems. Evaluating your digital authentication system can be made simpler and more cost-effective by employing existing standards and frameworks. For example, NIST SP 800-63 is a set of publications from .. Authentication Systems Decoded: The Science Behind Securing Your .. Authentication Systems Decoded: The Science Behind Securing Your Digital Identity by Deepak Gupta - Tech Entrepreneur, Cybersecurity Author on November 6, 2023 Imagine entering a cyber world where computer systems resemble vast metros bustling with information instead of people.
digital authentication system. How to Simplify Your Real Estate Authentication System - LinkedIn. Digital authentication is the process of verifying the identity and access rights of users who interact with online platforms and services. For real estate professionals and clients, digital.. elcr.adlsa.gov.qa. elcr.adlsa.gov.qa. Windows Authentication Overview | Microsoft Learn. The Windows operating system implements a default set of authentication protocols, including Kerberos, NTLM, Transport Layer Security/Secure Sockets Layer (TLS/SSL), and Digest, as part of an extensible architecture. In addition, some protocols are combined into authentication packages such as Negotiate and the Credential Security Support Provider.
digital authentication system. PDF D INSTRUCTION 8520 - Executive Services Directorate

Office of the Chief Information Officer Memorandum, "Interim Digital Authentication Guidelines for Unclassified and Secret Classified DoD Networks and Information Systems," . Approves alternatives to PKI for network logon and system authentication in accordance with DoDI 8520.03. h. Upon the request of the DoD PKI Program Management .. The Whys and Hows of Multi-Factor Authentication
digital authentication system. November 17, 2023
digital authentication system. The university requires all employees to use multi-factor authentication (MFA) -- an online security step that helps prevent unauthorized access to university systems. We recommend using Duo Mobile on your smartphone because its free, secure, and simple to use
digital authentication system. Duo Mobile creates no data on your device.. AUTHENTICATION Definition & Usage Examples | Dictionary.com
digital authentication system. Authentication definition: the act or process of establishing something as genuine or authoritative. See examples of AUTHENTICATION used in a sentence.
digital authentication system. Challenges and Solutions for Implementing Digital Authentication .. Digital authentication systems play an increasingly vital role in ensuring secure and reliable online transactions, especially in the Global South. However, small-scale shop owners in remote .
digital authentication system. ILoveQatar.net | Step-by-step guide: digital authentication of .